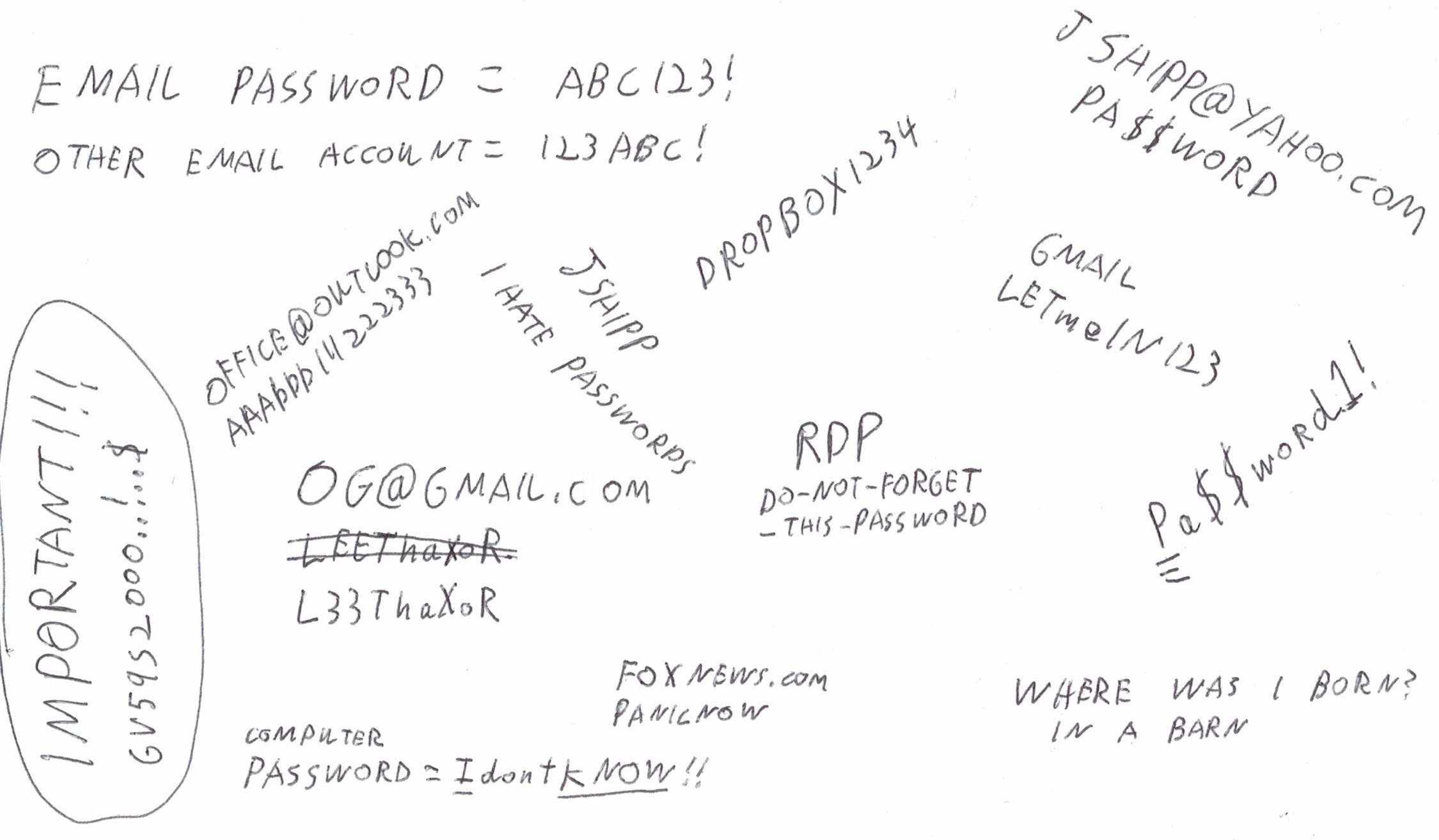
Painless Password Management Are passwords frustrating? Do you use the “I forgot my password” button on a regular basis? Do you believe your email account doesn’t have a password? Does your password database look like this?
There is a better way!!! Maybe one day, all websites will be able to scan our faces and know we are the rightful owner of our online identities, but that’s not going to happen this year, so we are stuck with a lot of passwords for the foreseeable future. Why can’t we just use the same password for everything? Well, there are 2 reasons. If you actually try to use the same password for literally every website, you will quickly discover some websites won’t accept your password because it’s not long enough, not short enough, has symbols, or doesn’t have symbols, or contains your username, or some other reason that you didn’t anticipate when you crafted your masterpiece. Secondly, it’s a terrible security habit to do so, because when a website gets hacked, hackers will get your password, and they will go to other websites and attempt to log in with it hoping you foolishly use the same password on other websites. When Yahoo got hacked in 2012 and didn’t tell anybody for 4 years, hackers had stolen 200 million passwords and were delighted to be able to log into so many people’s other email accounts, Facebook accounts, and even bank accounts with the same password. When MySpace got hacked, 360 million passwords were stolen. These data breaches happen WAY too frequently. I don’t think I can name 10 major websites that have NOT had a data breach in the past 10 years. Google has had several data breaches but none that leaked passwords (yet!). Microsoft has had several data breaches, including a Minecraft breach that leaked 6 million passwords. THIS IS WHY WE MUST NOT USE THE SAME PASSWORD FOR EVERY WEBSITE. Why can’t we use a clever algorithm to make each password unique but still be able to keep it in our brains? For example: This is a phase many people go through as their password management skills evolve, but this method has the same problem with some websites' password requirements not being compatible with your masterpiece algorithm, and you’ll find yourself struggling to remember the exceptions. You might be better off against hackers' automated scripts that go through stolen password lists trying to log in at various websites, but will a human hacker be able to guess your algorithm’s pattern and come up with passwords for your other websites? There’s a great website that is operated by a well-known security researcher that you can enter a password into to see if it has already been stolen in a website hack. https://haveibeenpwned.com/Passwords It’s relatively safe to enter your password into this site because your password is hashed before it is sent to the website’s back-end server to compare to all the stolen passwords. A hash is a way of converting a password into a different string of characters. It is mathematically impossible to convert a hash back into the original password, and this is why it’s safe to use this website. Any website that was built by programmers with at least half a brain will be using hashes in the website’s password database. This reduces the damage when the website gets hacked, but hackers have some powerful tricks they can use to convert the stolen hashes back into passwords. They can’t do it directly with math, but they can brute force them with rainbow tables (google that if you want to be terrified). Why can’t we just write our passwords down on a piece of paper and keep it under our keyboard? That’s actually a decent method. As long as you trust the people that have access to your keyboard, I’m not going to laugh at you for using a paper list. Your paper list will certainly be safe from Russian hackers, and it’s 1000 times better than trying to memorize passwords and using “I forgot my password” regularly. If you are going to use a paper list, there are some guidelines you should try to follow: I created a paper password template you can print and use. You can download it from: http://www.jshipp.com/articles/passwords.pdf The problems with paper passwords are: There is another way. You can keep your passwords on the computer. Modern web browsers such as Chrome and Firefox and Edge have built-in password managers. The #1 goal of these passwords is convenience, not security... These password managers recognize when you log into a website that isn’t already in your password database and nags you about adding it. When you go to that website’s login page in the future, the browser will automatically fill in your username and password. These password databases can even sync with a cloud server if you are logged into your browser. This is convenient, but you better bet the people working for the companies that own the cloud servers certainly can see your passwords. Are they going to do something evil with them? PROBABLY not... Are they going to get hacked and let hackers steal our passwords? Not frequently… These employees have probably been background checked and signed some papers officially promising not to do anything evil with these passwords. Do you want to trust a few strangers to keep a promise, or do you just want to NOT give them your passwords? This is where you are going to have to give up some of that convenience. Security and convenience have been in a holy war since the dawn of computers. It seems like most people let convenience win, but enough of that, or I’ll get on my soap box. The secret to having a truly secure password manager is to use what we call “trust no one” security”. This means you won’t be trusting ANY strangers with your passwords. To achieve this, your password database will need to be encrypted with uncrackable encryption. There are lots of free password managers out there that implement “trust no one” encryption, but I’m going to keep it simple for you and only tell you about my favorite one. It’s called BitWarden. They didn’t pay me a penny to recommend them. They earned my recommendation with pure awesomeness. Their code is open source, so you can inspect it yourself to confirm there are no back doors. Your passwords are encrypted and synchronized between all your computers and phones and tablets and Chromebooks and coffee makers, and best of all, it’s free! They make their money by charging a small amount for advanced features such as sharing password records with coworkers or family members. Bitwarden works as a website, a browser plugin, an android app, or an iPhone app. The browser plugin integrates tightly with your browser to help you save and autofill passwords. You will have a master password that decrypts your password data. It does not have a “forgot my password” feature. If you forget your master password, you are just going to be up the creek without a paddle. This is one of the features you have to give up if you want "trust no one" security, because if YOU can get to your passwords without your password, then strangers can too! It’s fireproof, theft-proof, stays sorted, never runs out of space, and can even be accessed from that library computer, so you no longer have an excuse to be struggling with passwords. One last thing. When you use a computerized password manager, you have a much better way to generate strong unique passwords for each website. Any decent password manager is going to have a random password generator built in. There is no reason you shouldn’t be generating 40-character random gibberish passwords for each website, especially when you will never be typing them. Bonus tip. Do you realize your email password is one of your most important passwords? What happens when you go to your bank’s website and click “forgot password”? They EMAIL you a link to reset your password! This means when a hacker gets into your email account, they can get into pretty much ALL of your accounts! This is why I recommend enabling 2-factor authentication for your email account, as well as any account that can transfer money away from you, and any other accounts you feel need to be high security. 2-factor authentication means you will be asked for a 2nd password when logging in, and this 2nd password changes every time. You’ll get this 2nd password from a text message or authentication app. I recommend NOT using text messages for your 2nd factor because they are vulnerable to sim-jacking, which is a whole nother chapter, but it’s basically where a hacker tricks your cellular service provider (like VerizonWireless) into transferring your phone number to the hacker’s phone, so the hacker can read your text messages. You made it to the end! Now go improve your password management! I better not see you taking more than 10 seconds to find a password!
|