I hate to start a panic, but … um .. PANIC NOW!!! UPDATE 6/2016 - There is a website you can upload your encrypted files to, and it will attempt to identify which ransomware you have, and let you know if there is a known way to decrypt all your files for free.
UPDATE 11/2015 - I found a way to totally prevent this virus and all its variants.
On Oct 30, 2013, I saw the worst computer virus in my career. This is a whole new level of bad. This virus has the ability to cause unprecedented damage. If you get it, you might lose ALL your important data, and I might not be able to recover it!
The virus came via email from [email protected] with the subject “past due invoice”. (this doesn't mean it will come in like this in the future.) When the victim opened the attached "invoice", the virus encrypted (scrambled) all the data on the victim’s computer, as well as data on the local file server the victim’s computer was connected to. The virus then demanded $300 to have the data unencrypted. It was impossible to unencrypt the data without paying the $300 ransom, because the virus used 2048-bit RSA encryption, which is the same technology that protects you from hackers when you log into a secure website, like your bank. I could have cleaned the virus very easy, but we still would have had the problem of the data being encrypted. After a lot of consideration, the victim decided the data was worth $300, so we paid them, as bad as we hated to. After about a day of nervous waiting, the victim's computer automatically decrypted the files, and removed the virus. This virus is called CryptoLocker.
If you think you are safe because you do backups, you might have to think again.
Backups that ARE useful against this virus:
Shadow Copies? What's that? - Win XP (Home and Pro) - doesn't have shadow copy. - Win 7 PRO - makes shadow copies automatically, and allows you to access them by clicking START, click COMPUTER, right click your C drive, Click PROPERTIES, Click PREVIOUS VERSIONS. - Win 7 Home - You should be able to access Win7 shadow copies by using one of these programs
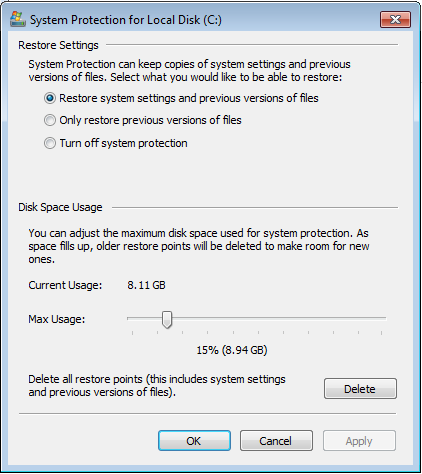
- Win 8 - You should be able to access Win8 shadow copies by using this program (http://www.shadowexplorer.com/downloads.html) If you do not use UAC properly, the virus WILL delete all the shadow copies too. Using UAC properly will successfully prevent the virus from deleting the shadow copies, but you still lose any data that was modified since the last shadow copy. Using UAC in Windows 7 like I recommend in my basic UAC article will give you PARTIAL protection, when combined with a useful backup. Using SRP will give you full protection! Using UAC like I recommend in my advanced UAC article will also give you FULL protection but it's not as convenient as using SRP. Also, if the amount of data encrypted exceeds the amount allocated for shadow copies, windows WILL delete all the shadow copies! For example, if you have 5GB of pictures on a 80GB hard drive, and shadow copies are set to 5%, you are going to lose all your shadow copies if you get this virus. If you are running Win7, you should check to see what percent your computer has allocated for shadow copies, click START, right click COMPUTER, click PROPERTIES, click SYSTEM PROTECTION, click your C drive, click CONFIGURE.
I like to set it to 20%. Shadow copies are awesome because this is the only way that a lot of people have to get their data back without paying, but you shouldn't trust your data to it completely since it can let you down in certain situations. FOR ADVANCED USERS trying to restore from shadow copy:
Other Links: http://en.wikipedia.org/wiki/CryptoLocker http://www.snopes.com/computer/virus/cryptolocker.asp https://www.decryptcryptolocker.com/
|